WHAT WE DO
PENETRATION TEST
Highly-ethical standard and solid experienced of our certified team can provide a full range of security assessment services to meet your requirement.
RED TEAMING
We will bombard your security controls from adversaries' perspective in order to measure your security capabilities and train your people.
CONSULTING
Developing and maintaining effective information security strategy and standard can be difficult without experienced individuals. Incognito Lab's consulting services are set to be your partner.
TRAINING
Incognito Lab team develops training courses and brings our knowledge to help organisations secure their business.
WHAT'S NEW
ARTICLES
Mar
09
2026
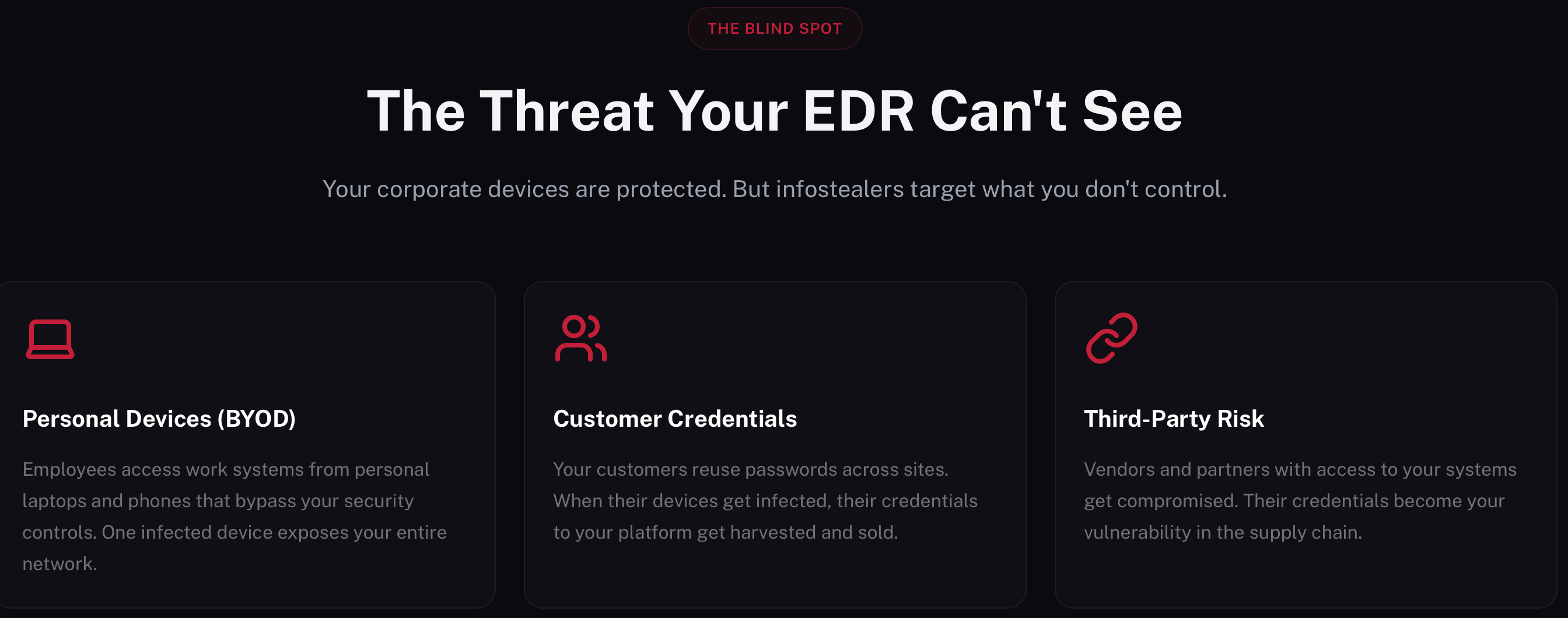
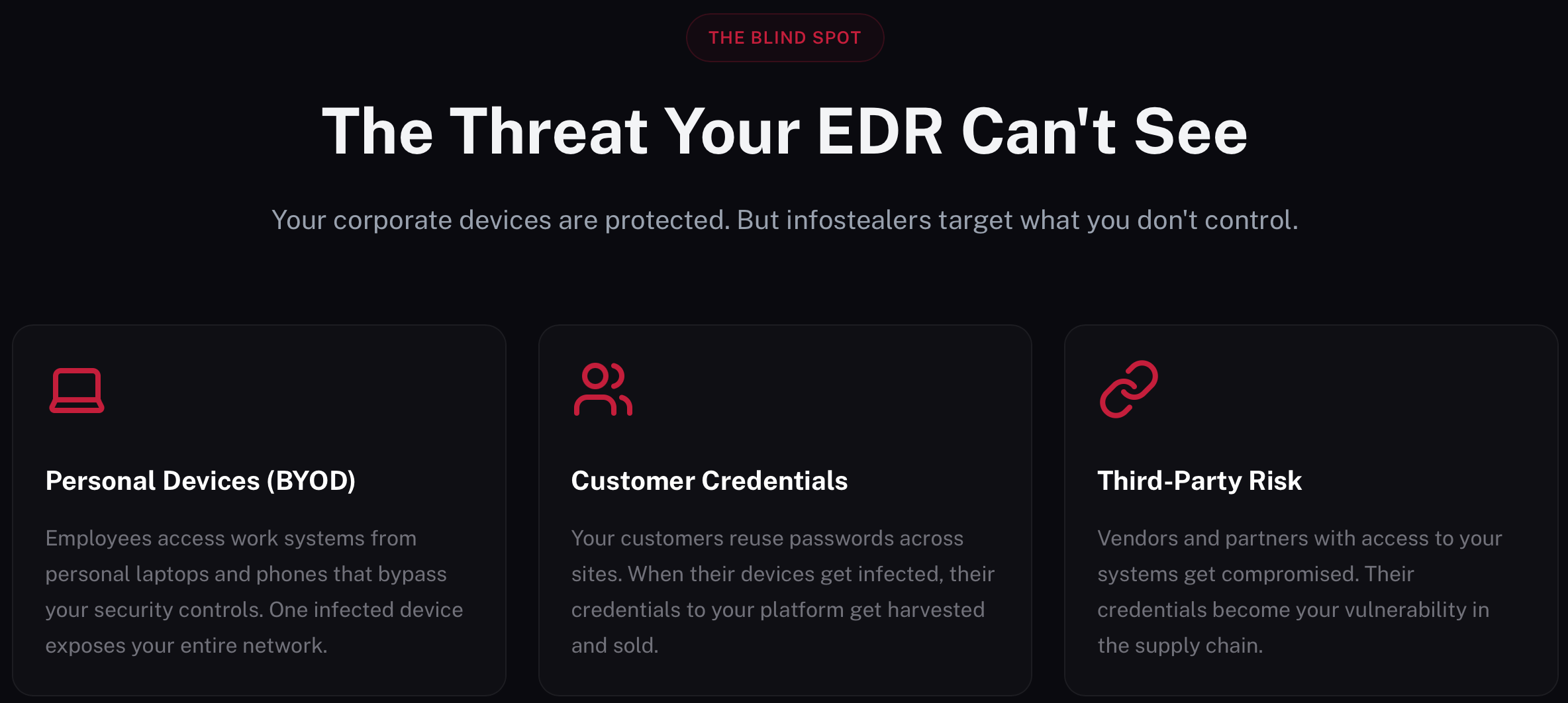
Why EDR Isn’t Enough: A Guide to Monitoring Infostealer Logs with RedAlert
Hackers no longer break in—they log in. Discover how RedAlert provides visibility into leaked credentials from unmanaged devices and the dark web, closing the security gaps that traditional EDR and Antivirus miss.
READ MORE

ARTICLES
Feb
20
2026
Cyber Security Checklist on Digital House
คนเรามักจะเลือกล็อกประตูบ้านเพื่อความปลอดภัย.. แล้วบ้านของคุณในโลก 'ดิจิทัล' มีการล็อกที่แน่นหนาแล้วหรือยัง?
READ MORE
ARTICLES
Feb
20
2026
Snowflake Breach 2024: เมื่อ Infostealer กลายเป็นภัยเงียบที่ EDR มองไม่เห็น
เจาะลึกภัยร้าย Infostealer และ Stealer Log ผ่านกรณีศึกษา Snowflake Breach 2024 ทำไมเครื่อง 3rd Party ถึงเป็นจุดอ่อนสำคัญ? พร้อมแนะนำ RedAlert บริการเฝ้าระวังเชิงรุกจาก Incognito Lab เพื่อปิดช่องโหว่ที่ EDR มองไม่เห็น
READ MORE
WHO WE ARE
LIFE AT ICL
JOIN US
WHY INCOGNITO LAB
100%
SUCCESS RATE
180+
NO. OF OUR CLIENTS
20
CYBER DRILLS **NOT PHISHING
14
YEARS OF APPEARANCE
0
BLANK PENTEST REPORT
AWARDS AND RECOGNITIONS






CERTIFIED PROFESSIONALS












Certified Information Systems Security Professional (CISSP)
GIAC Security Expert (GSE)
GIAC Penetration Tester (GPEN)
GIAC Certified Forensic Analyst (GCFA)
eLearnSecurity Certified Professional Penetration Tester (eCPPT)
EC-Council Certified Ethical Hacker (CEH)
CREST Registered Penetration Tester (CRT)
AWS Certified Security - Specialty
Certified Information Systems Auditor (CISA)
GIAC Exploit Researcher and Advanced Penetration Tester (GXPN)
GIAC Mobile Device Security Analyst (GMOB)
GIAC Certified Intrusion Analyst (GCIA)
eLearnSecurity Web Application Penetration Tester (eWPT)
EC-Council Certified Security Analyst (ECSA)
Offensive Security Certified Professional (OSCP)
AWS Certified Solutions Architect - Associate
Certified Information Security Manager (CISM)
GIAC Web Application Penetration Tester (GWAPT)
GIAC Reverse Engineering Malware (GREM)
GIAC Security Essentials (GSEC)
eLearnSecurity Certified Threat Hunting Professional (eCTHP)
CREST Practitioner Security Analyst (CPSA)
Offensive Security Certified Expert (OSCE)



